PolicyGlass

Documentation: policyglass.cloudwanderer.io
PolicyGlass allows you to analyse one or more AWS policies’ effective permissions in aggregate, by restating them in the form of PolicyShards which are always Allow, never Deny.
PolicyGlass will always result in only allow PolicyShard objects, no matter how complex the policy. This makes understanding the effect of your policies programmatically a breeze.
Try it out
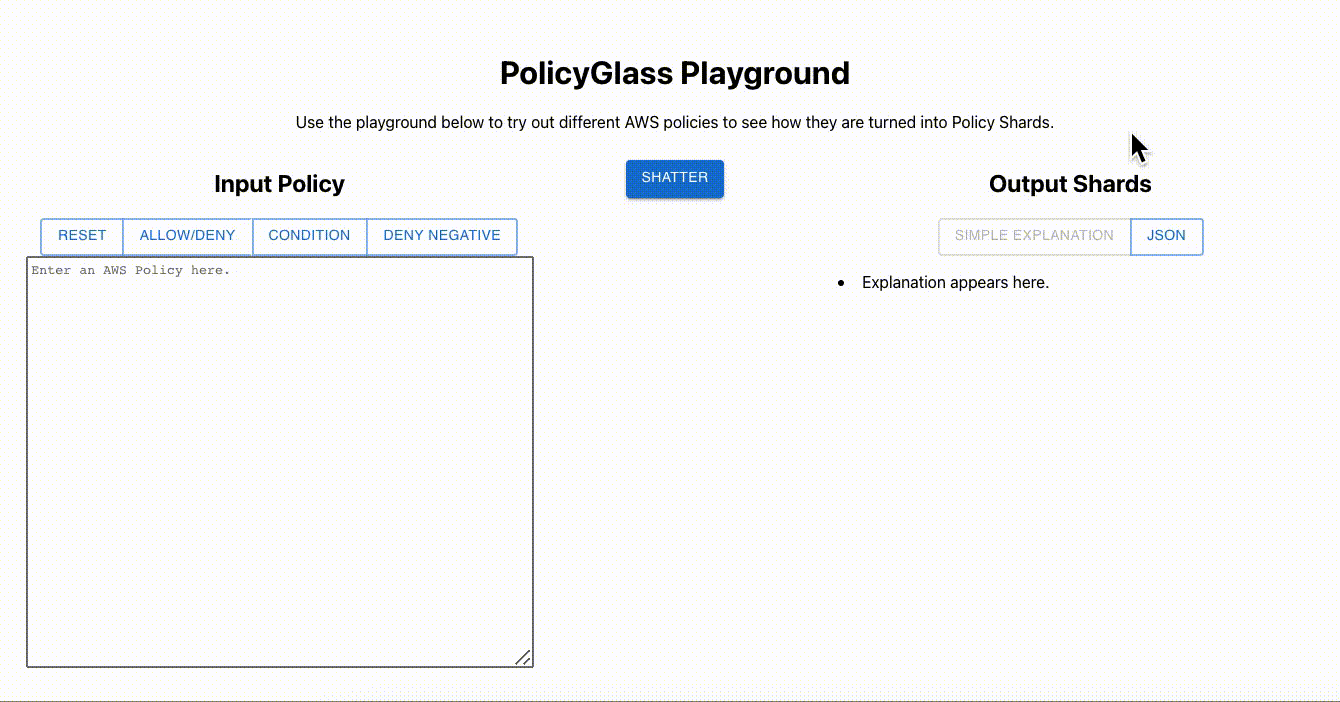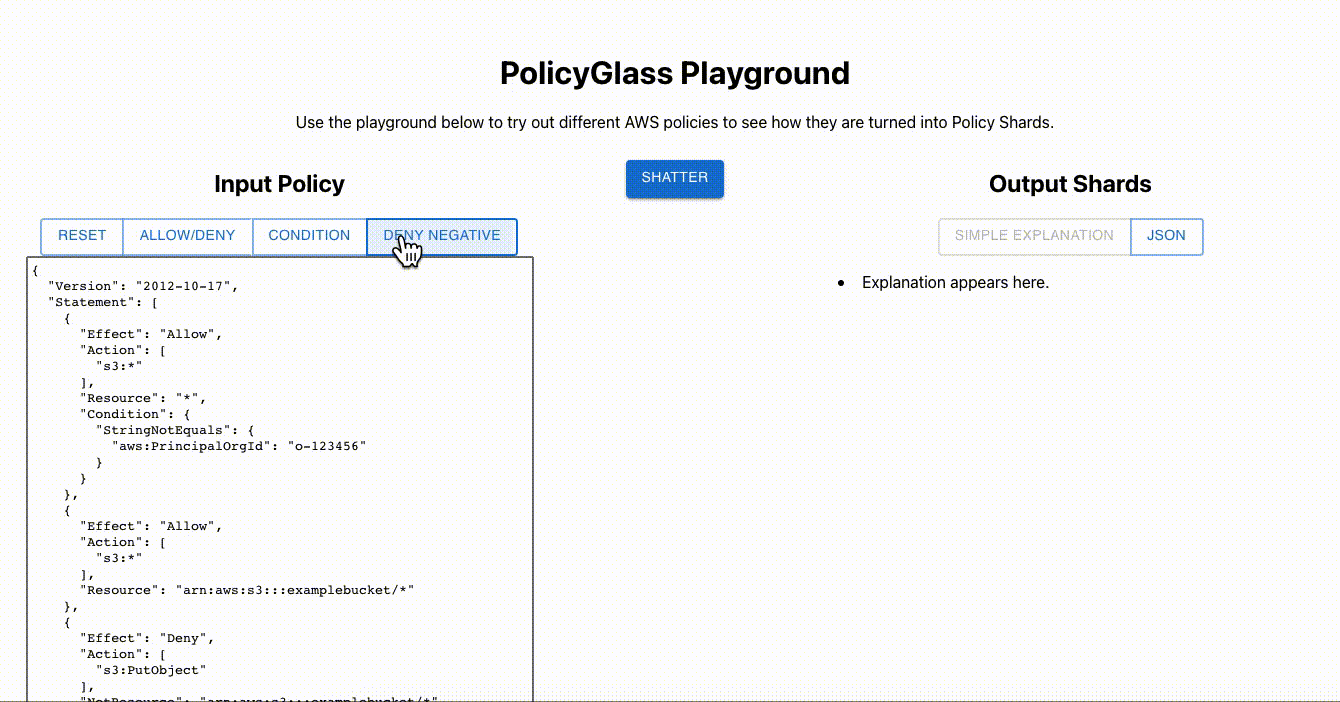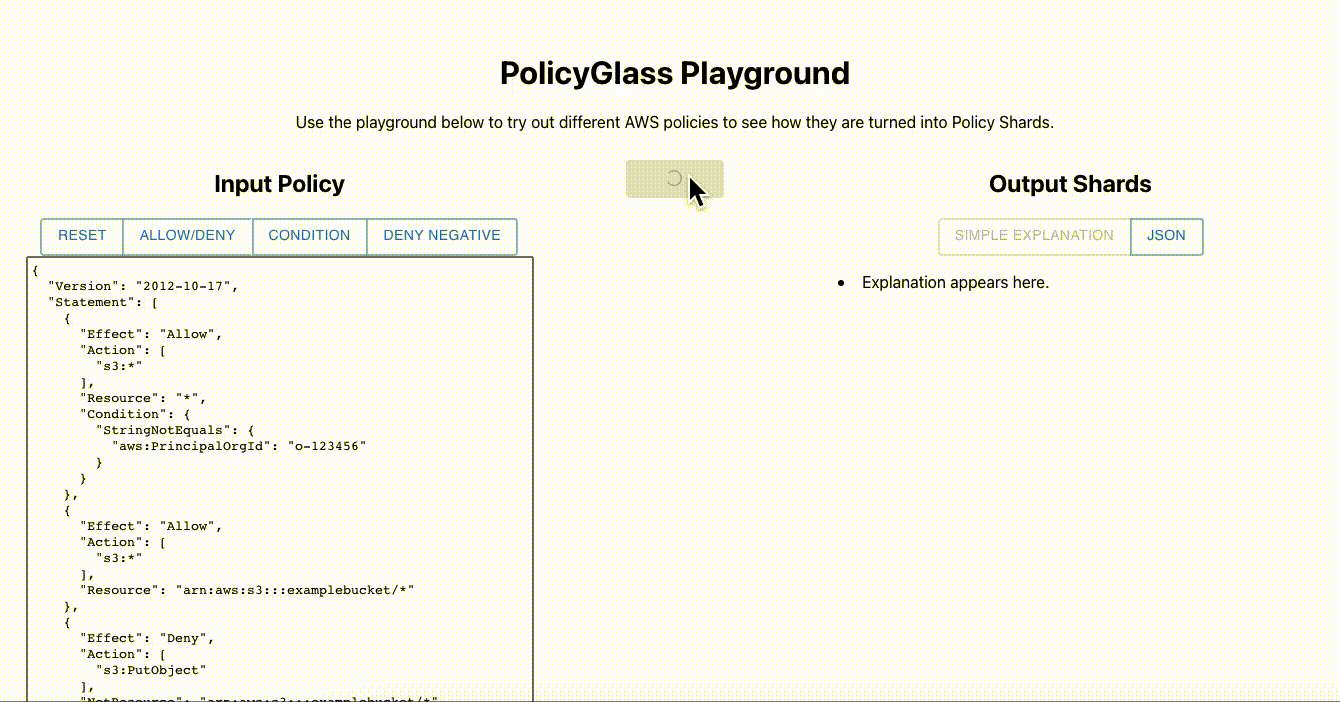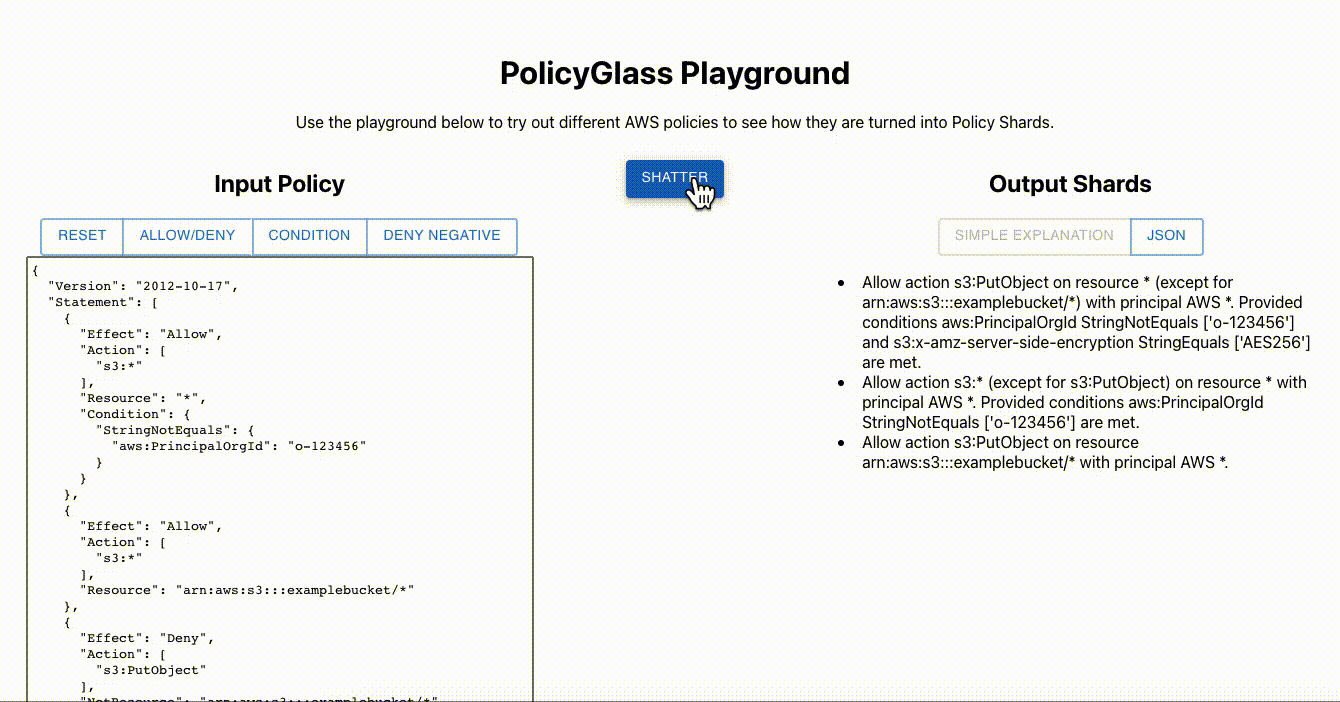
Try out custom policies quickly without installing anything with the PolicyGlass Sandbox.
Installation
pip install policyglass
Usage
Let’s take two policies, a and b and pit them against each other.
>>> from policyglass import Policy, policy_shards_effect
>>> policy_a = Policy(**{
... "Version": "2012-10-17",
... "Statement": [
... {
... "Effect": "Allow",
... "Action": [
... "s3:*"
... ],
... "Resource": "*"
... }
... ]
... })
>>> policy_b = Policy(**{
... "Version": "2012-10-17",
... "Statement": [
... {
... "Effect": "Deny",
... "Action": [
... "s3:*"
... ],
... "Resource": "arn:aws:s3:::examplebucket/*"
... }
... ]
... })
>>> policy_shards = [*policy_a.policy_shards, *policy_b.policy_shards]
>>> effect = policy_shards_effect(policy_shards)
>>> effect
[PolicyShard(effect='Allow',
effective_action=EffectiveAction(inclusion=Action('s3:*'),
exclusions=frozenset()),
effective_resource=EffectiveResource(inclusion=Resource('*'),
exclusions=frozenset({Resource('arn:aws:s3:::examplebucket/*')})),
effective_principal=EffectivePrincipal(inclusion=Principal(type='AWS', value='*'),
exclusions=frozenset()),
effective_condition=EffectiveCondition(inclusions=frozenset(), exclusions=frozenset()))]
Two policies, two statements, resulting in a single allow PolicyShard.
More complex policies will result in multiple shards, but they will always be allows, no matter how complex the policy.
You can also make them human readable!
>>> from policyglass import explain_policy_shards
>>> explain_policy_shards(effect)
['Allow action s3:* on resource * (except for arn:aws:s3:::examplebucket/*) with principal AWS *.']

